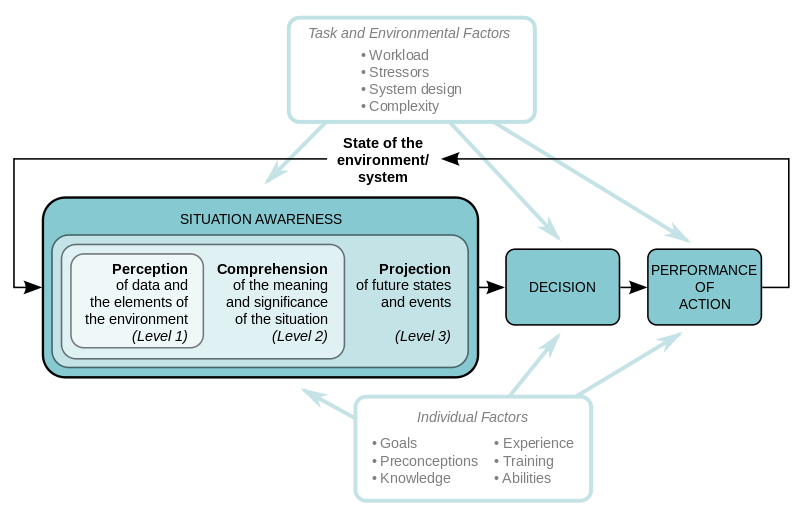
If you don’t have a reliable and authoritative repository of the devices connected to your network, their posture and the use of privileged accounts, it is difficult to believe that you really have any hope of managing them well to protect your organization’s sensitive information. If you are not managing IT security risk well, it will have an effect on all aspects of enterprise risk. This is why situational awareness needs to be a top enterprise focus.
The first category in the NIST Cybersecurity Framework is “Identify”. The first 5 CIS controls related to discovery, inventory and posture of endpoints, software and privileges. Read More
Posted in Blog, Cybersecurity & Infosec, Risk Management, Vulnerabilities
https://www.scmagazine.com/this-months-patch-tuesday-fixed-bug-that-could-exploit-authentication-in-microsoft-remote-desktop-protocol/article/750777/
Posted in Vulnerabilities
https://www.scmagazine.com/the-vulnerabilities-included-a-user-after-free-and-type-confusion-vulnerability-which-could-both-result-in-remote-code-execution-if-exploited/article/750776/
Posted in Vulnerabilities


