I am going to share some thoughts with you. My point of view. This should lead into some articles I plan to write on various topics. These will probably lead to presentations and podcasts over the next few months.
• IoT/IIoT/ICS: In particular related to industrial IoT (IIoT) and ethical conundrums related to consumer IoT. Compare and contrast IT/OT and IoT, IIoT, ICS-SCADA. What are the problems we need to solve?
• Artificial Intelligence: OK. No Turing test (yet)! However, we all need to get on the same page around AI, machine learning, deep learning. What is it, what problems can it solve or help us get a better handle on? (Spoiler: We have a projected need for 2-3 million US cybersecurity professionals in the next 1-2 years, but as velocity and volume of attacks exponentially increases, we must break the cycle of throwing more security analysts at the problem. We need AI as a force multiplier!) How are the adversaries using AI and automation to their advantage? Also, cut through the BS and buzzwords to get at the REAL value of AI in the future.
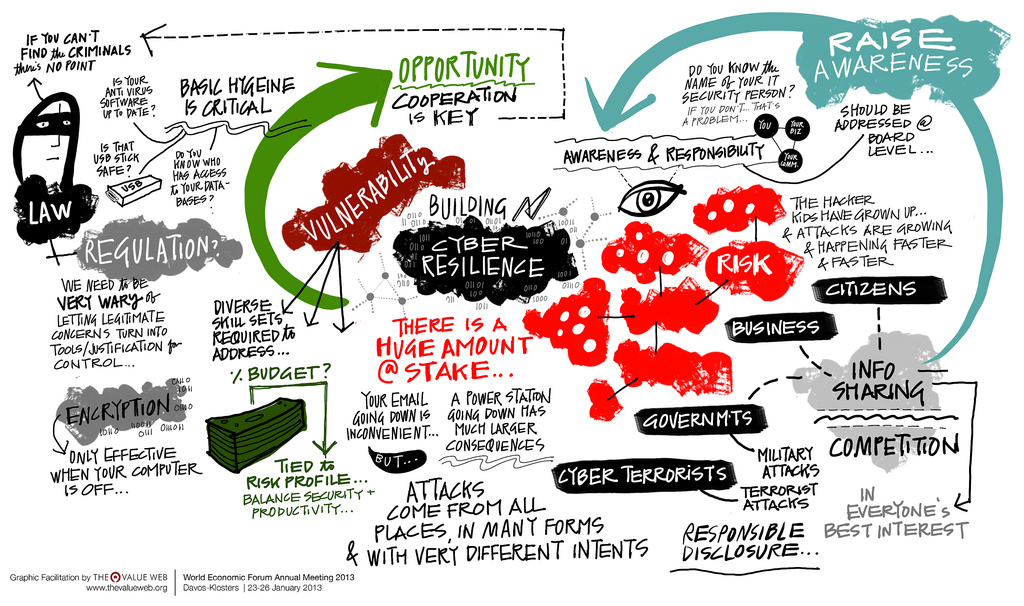
• Situational Awareness: How can we have pudding if we don’t eat our meat? By which I mean, if we don’t know the posture/exposure of our assets and privileges, how can we protect and monitor them? CIS critical security control #1 is: asset inventory. The first pillar of the NIST Cybersecurity Framework is Identify. Assets may include endpoints, other devices, apps, identity, privileges, data…. For example: What software and OS is installed on every asset? What version? What is the drift from a secure baseline configuration? Who has access to what? Where is the critical data (things of value)? What is the impact if the asset becomes unavailable or corrupted? Once we know our real exposure in real-time, then we can respond faster to threats and protect value at risk better. Then, I posit, we have a realtime view to enterprise (IT security) risk. Then, we can best leverage threat intelligence on our adversaries.
• Security Fundamentals 101: What are the fundamentals we better get right, if we expect to mature our security program? I suggest we anchor to standard frameworks and secure baseline configurations, and apply proper hygiene. What does that entail?
• Value at Risk: How do we determine what matters in the context of our organizations, so we can focus on protecting what matters most? Prioritizing our security resource allocation (people/process/technology) based on actual risk calculations and knowing the value of assets (data, apps, assets, identity).
• Blockchain: What is blockchain and why should you care? Here’s another overused buzzword. There are times where blockchain may ensure the integrity of processes (think elections, code, forensic data…) and there are other use cases where it won’t add any value and may cause more problems than it solves. What happens when blockchain insecurities surface? Will there be one blockchain to rule them all?
• Automation and Orchestration: Automation may utilize AI, but there is much more to automation than meets the eye. Automation and orchestration are needed to reduce the human workload and more securely deploy and manage assets/apps, on-prem and in the cloud, and to respond faster to attacks by adversaries.
• Defense is Not Dead: Defense in depth is still very necessary. It is not going away or morphing into Detect/Respond. The (via Ponemon/2018) time to detect a breach is still 191 days on average. This is too long. We do need to detect much faster and way better… but, how we prioritize our resource spend and our cybersecurity maturity model depends on our risk profile viewed in the context of our organizational objectives and regulatory pressures. Just HOW do we Identify, Protect, Detect, Respond and Recover. All 5 CSF pillars are necessary.
• Cybersecurity Resilience: This will be a multi-part series to cover what it takes to be ready for new disruptive technologies, new uses of technology, new business process and regulations, and an ever increasing volume/velocity/sophistication of attacks. It will incorporate some topics I called out above.
• How do I define Cybersecurity Resilience and what motivates its necessity? What I the problem it is trying to solve?
• What is a capability maturity model and how do I know the optimal maturity level for (different functions inside) my organization?
• The answer to that is by taking a risk-based approach and focusing on value at risk, in the context of your organization. How do I really measure risk? How do I express IT security risk to the board, so they can understand it and compare it to other enterprise risks? [See: Value at Risk above]
• Basic Hygiene: What is it? Where do I start? Introduce CIS 20, secure baseline configurations and anchoring to standard frameworks such as NIST CSF. [See: Security Fundamentals 101 above]
• Situational Awareness: Where are my assets (devices, data, identities, apps, privileges…) and what is their exposure? What is unpatched or misconfigured? What suspicious traffic and payloads and authentications am I monitoring on my network or with assets off-network and in the cloud? What is my threat intelligence telling me about new threats and exploits that might affect value at risk? [See: Situational Awareness above]
• How do I attract and retain a security workforce? How do I train and develop security staff? How do I build a security culture in my organization?
• What skills are required of the CISO? What is necessary in security leadership?
• What new tools and approaches will be necessary to be resilient as the threat landscape evolves at a faster pace in the future? Can we flip the signal to noise ratio and raise the economic cost for our adversaries?
Saying “you don’t need to outrun the bear, just outrun your neighbor” is stupid and shortsighted. We are all continuously under attack, and the attacks are getting faster and more sophisticated. The Internet is full of bears (adversaries). You need to mature your security program. Doing this in a holistic way, aligned with business objectives, is what I mean when I say cybersecurity resilience.




