
Artificial intelligence (AI) and machine learning (ML) have been increasingly used as product marketing buzzwords. Nevertheless, I feel certain that AI is an integral part of how we approach cybersecurity in the future, with particular applications for securing manufacturing environments.
See John’s earlier article on Securing the Industrial Internet of Things. Read More
Posted in AI & Machine Learning, Blog

Why are we paying attention to our online privacy now? In March 2018, it was discovered that Cambridge Analytica had been harvesting Facebook user information, and using it to build voter profiles which they then sold off to groups who wanted to influence the 2016 Presidential Election.
The issues we are facing today aren’t new. The Internet puts your personal information at risk: on your computer and mobile devices, in email and social media. It just becomes harder to protect your privacy and personal information, as the Internet and social media become more complex. Read More
Posted in Blog, Community, Cybersecurity & Infosec, Privacy
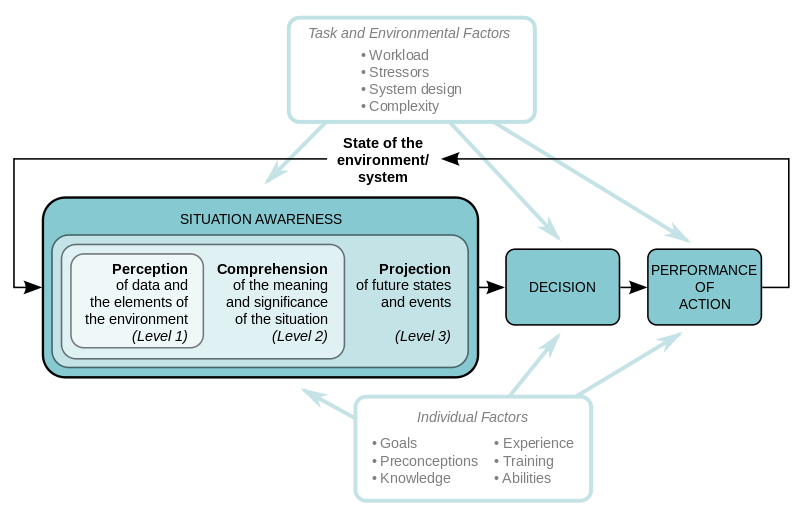
If you don’t have a reliable and authoritative repository of the devices connected to your network, their posture and the use of privileged accounts, it is difficult to believe that you really have any hope of managing them well to protect your organization’s sensitive information. If you are not managing IT security risk well, it will have an effect on all aspects of enterprise risk. This is why situational awareness needs to be a top enterprise focus.
The first category in the NIST Cybersecurity Framework is “Identify”. The first 5 CIS controls related to discovery, inventory and posture of endpoints, software and privileges. Read More
Posted in Blog, Cybersecurity & Infosec, Risk Management, Vulnerabilities

The NIST Cybersecurity Framework has five categories for enterprise security: Identify, Protect, Detect, Respond, Recover. There is a lot of focus on Detect and Respond as the new shiny. Let’s be honest, every company should be doing their due diligence in all five of these categories. While traditional protection controls are less effective, we still need to be doing what we can to identify and protect (let’s face it, we used to rely on static antivirus and today it is laughable to suggest static AV is anywhere adequate protection for endpoints).
I’ve heard people say that we don’t need defense in depth, we need to detect in depth. I’m not sure what that means. I agree we need to do a better job of detecting faster and responding better, but we only have two options here, DEFENSE and OFFENSE. I really don’t hear enterprise CISOs suggesting we attack back. Not sure the general counsel would agree on that either. Read More
Posted in Blog, Cybersecurity & Infosec
One of the most frequently maligned and misused terms by information security vendors is: Artificial Intelligence (AI). AI and machine learning (ML) are, however, not a passing fad. Let me define these terms in more details.
Artificial intelligence has been the subject of sci-fi novels for several decades now. Computer systems with “brains” to rival or surpass that of humans. The idea that AI systems are “thinking machines” that in any way rival the human brain, is fiction. At least in the near future. Read More
Posted in AI & Machine Learning, Blog

We have may concerns today regarding security and privacy, but our concerns will only be magnified in the future. In this presentation I look forward 10, 20 and 30 years into the future at trends, issues and possible solutions. (My notes for #CERIAS20 futurist panel.) https://is.gd/CERIASfuture18
Posted in Blog, Presentations & Webinars
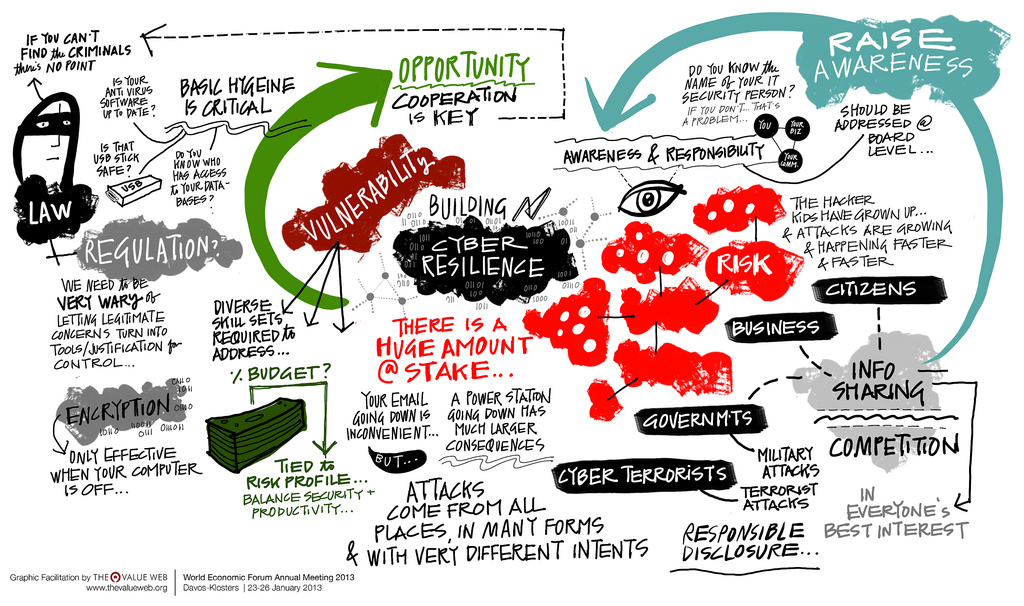
I am going to share some thoughts with you. My point of view. This should lead into some articles I plan to write on various topics. These will probably lead to presentations and podcasts over the next few months.
• IoT/IIoT/ICS: In particular related to industrial IoT (IIoT) and ethical conundrums related to consumer IoT. Compare and contrast IT/OT and IoT, IIoT, ICS-SCADA. What are the problems we need to solve? Read More
Posted in Blog

August 11th, 2017 by John
CornCon Kids’ Hacker Camp (The Children of The CornCon) will feature dozens of kid-friendly activities in 2017. These activities range from lock picking and dumpster diving, to learning about electronics, coding and blacksmithing. The intention of the kids’ camp is to open the eyes of kids to the benefits and vulnerabilities of technology. This is done every fall in the Quad Cities, 100 kids at a time.
For the first time, kids at “CornCon 3: The Courne Ultimatum” will be able to “Hack The Pentagon”. This program started as a bug bounty, developed by the DoD to uncover vulnerabilities in their computer systems and web applications. The program uncovered 138 vulnerabilities and now the U.S. Army Cyber Command is sending First Lieutenant Daniel Lim on the road to show kids and adults how bug bounty programs work, and the methods used by penetration testers to uncover and responsibly report vulnerabilities. Responsible disclosure is key, as finding and exposing vulnerabilities to the public can lead to malicious attacks, if it is not preceded by software patches to address the vulnerability first. Read More
Posted in Blog, Community








